These are the most feared hacker groups in the world
"Advanced persistent threat" actors are frequently discussed as a hot topic among cybersecurity experts, political leaders, and white hat hackers.

It's the best way to define the hackers who burrow into networks and maintain "persistence" — a connection that can't be stopped simply by software updates or rebooting a computer.

APTs vary in their methods of gaining access. Some use targeted email phishing campaigns that install malicious software onto a victim's machine, while other, more advanced groups will use "zero-day" exploits.

The exploits are called "zero day" since no one knows about them until they are actually used for the first time. The software bugs were unknown, and the victim has had zero days to develop a solution to it.

One such nation-state APT used four such zero-days in an attack against Iranian nuclear sites. One is usually enough to get the job done, so four is pretty much unheard of.

And zero days are also a big business in itself. These software exploits can be bought and sold for hundreds of thousands, and sometimes millions of dollars.
Though sometimes it can be very hard to determine who an APT is, where they came from, or if they even have the backing of their nation's government.

That's due to the problem of attribution, since hackers can hide behind multiple proxies and bounce their traffic around different computers around the world. A North Korean army hacker could be attacking South Korea with a computer it hacked previously that was located in Japan, for example.
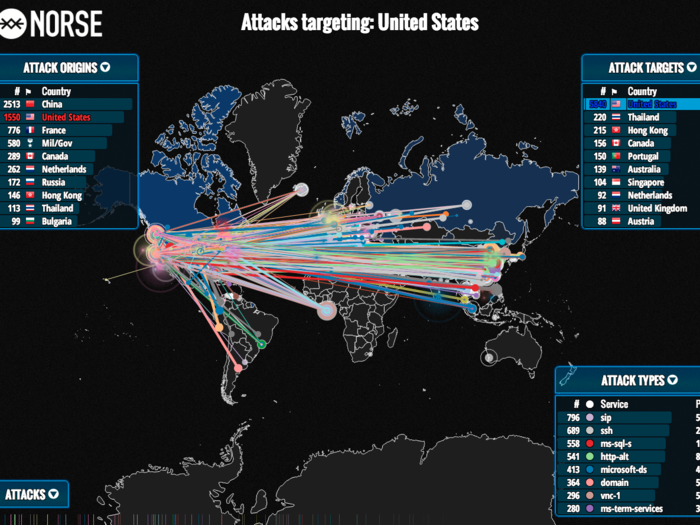
Still, their techniques, tactics, and procedures usually offer at least some insight. And cybersecurity companies like Mandiant, Crowdstrike, Kaspersky Labs, Symantec, and others often give them names and detail who they *think* they are.

One thing that's very clear when researching known APTs: China seems well ahead of everyone else. There are more than 50 groups with ties to the country, far more than Russia — which has roughly a dozen.

Perhaps the most notorious among China's APT groups is known as "Comment Crew." The cybersecurity firm Mandiant released a 60-page report in 2013 linking it to attacks on Coca-Cola, RSA, and US critical infrastructure.

Source: The New York Times
The report offered up plenty of evidence that "Comment Crew" — sometimes referred to as "Comment Panda" or "APT 1" by other firms — was actually a Chinese military unit known as PLA Unit 61398.

Not surprisingly, China denied any involvement.

There are a number of Chinese groups operating in cyberspace. They've been given names like Naikon, Shell Crew, or Toxic Panda, and they've hacked everything from US government agencies to financial services and energy firms around the world.

Though China seems to have the most hacking units, other countries are doing their own attacks in cyberspace while trying hard to cover up their digital tracks.

One of them is the United States. As the disclosures from the Edward Snowden leaks have showed, the NSA's offensive hacking abilities are among the best in the world.

One of its unique methods was exposed in the leaks: NSA's top hackers actually intercept network hardware and computers and install "beacons" to give them a backdoor inside. Then they box it back up and send it on to the intended recipient.
Most cybersecurity experts believe it was NSA (along with Israel's Unit 8200) that built the Stuxnet worm, a sophisticated cyber weapon that physically destroyed Iranian centrifuges.

And a recent film called "Zero Days" also exposed how NSA could have totally wiped out Iran's infrastructure, from its power grid to financial sector, with nothing more than computer code. No small feat, for sure.

Iran was taken by surprise by Stuxnet, and it invested in its own offensive cyber army as a result. With $20 million in funding and a few years of experience, it now has the fourth largest cyber army.

Source: TI
Besides hackers launching cyberattacks on US financial institutions a few years ago, an Iranian group called "Shamoon" pulled off a major hack of Saudi Aramco, wiping out or totally destroying around 35,000 computers used by the state-owned Saudi Arabian oil firm.

Source: TI
They’ve grown up very fast and very significant over the past few years," David Kennedy, the CEO of cybersecurity firm TrustedSec, told Tech Insider. "They realize they can’t have any type of superiority around air, or anything like that, especially when it comes to the United States. So they’re investing a lot of it into the cyber piece.

Another key player is Russia, which has about a dozen APT groups with names like "Sandworm," "Cozy Bear," and "Turla Group." The most notorious among them is called "Sofacy."

Also referred to as "Fancy Bear" by cybersecurity firm Crowdstrike, it was most recently found inside the servers of the Democratic National Committee. The firm also found "Cozy Bear" there as well, writing that both groups' "tradecraft is superb, operational security second to none and the extensive usage of ‘living-off-the-land’ techniques enables them to easily bypass many security solutions they encounter."

Source: Crowdstrike
Just last month, Palo Alto Networks observed Sofacy hackers as they sent phishing emails targeting the US government. The group — believed to be linked to the Russian intelligence service — mostly targets Russian neighbors, governments in Europe, and NATO.

Source: Palo Alto Networks / FireEye
Though another Russia-linked group called "Sandworm" has even the NSA director spooked about potential critical infrastructure hacks. That's because those seem to be the the team's specialty, and late last year, it used malware against a Ukrainian power company and turned off power for about 7 hours.

Source: iSight Partners
If there's one thing to take away from the big hacks and APTs that are pulling them off, it's that war and espionage in cyberspace continues in the shadows, with little in the way of rules of engagement.

There is no international standing or framework that is binding over any one nation-state in terms of offensive cyber operations," Bradley P. Moss, a national security lawyer, told Tech Insider in May. "It's whatever rules we put in place for ourselves.

It's the digital equivalent of the wild west. And it doesn't seem like it'll get better any time soon.

Popular Right Now
Advertisement