Similarly, scammers string together phishing attacks by compromising small, vulnerable businesses and leveraging their trust with larger business partners they work with.
"Instead of the email coming from 'someone at gmail.com' or some random address, it actually comes from a business that they work with. In phishing it's all about gaining the trust of the email, the reader, so that they click on it. And if it is a credential thing that pops up, they just give their credentials," Ganacharya said.
The old-school tactic of "typosquatting" is also seeing a resurgence among hackers, according to Ganacharya.
"Typosquatting is big again," Ganacharya said.
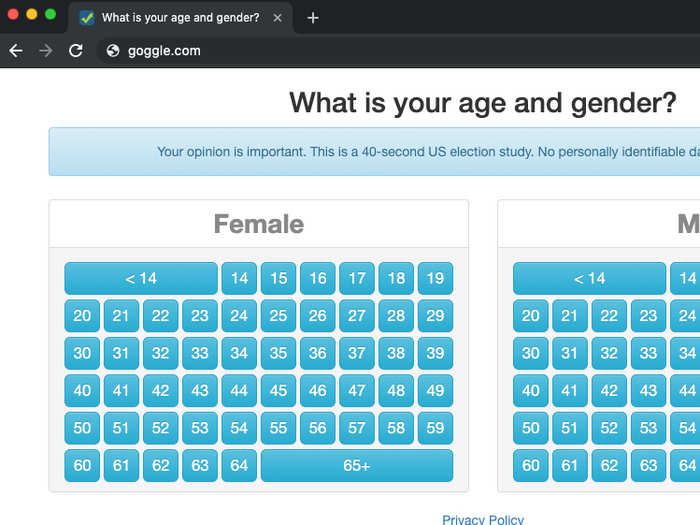
In this phishing scheme, also known as URL hijacking, attackers buy domains that are slight misspelling of popular websites, like goggle.com or yuube.com. The tactic was a mainstay of the early days of the internet, but has recently seen a resurgence.
"Spear phishers" put extensive effort into targeting a specific person, often creating multiple misleading pages to trick them.
Hackers will sometimes create fake social media pages or personal blogs for the persona they're using to target someone, intentionally adding their targets' friends in an effort to seem more trustworthy.
Fake credential pages are becoming more sophisticated.
Hackers will regularly make fake sites that mimic the login screens of trusted services, like email accounts. Ganacharya's team has built machine-learning systems that detect subtle differences in the appearances of the sites and flag them as fraudulent, but he said hackers are constantly building workarounds.
"If the attacker created a similar looking page [to a legitimate login screen], but then they were not able to match a font here and there or something is moved by one pixel, the machine learning models can pick that up," Ganacharya said.
A cottage industry of phishing-as-a-service is booming as scams become increasingly profitable.
Sophisticated hackers are now willing to sell their services to specific organizations, individuals, or nation-state entities who want to steal information from someone.
Some phishing-as-a-service providers offer networks of bots that proliferate fake websites, while others sell phishing toolkits to clients, according to Ganacharya.
"If you have the funding, you can go buy a phish kit or sign up for phishing as a service and they will build everything for you, and you just have to hope your payoff comes out higher than what you were paying the phishing-as-a-service company," Ganacharya said.